1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
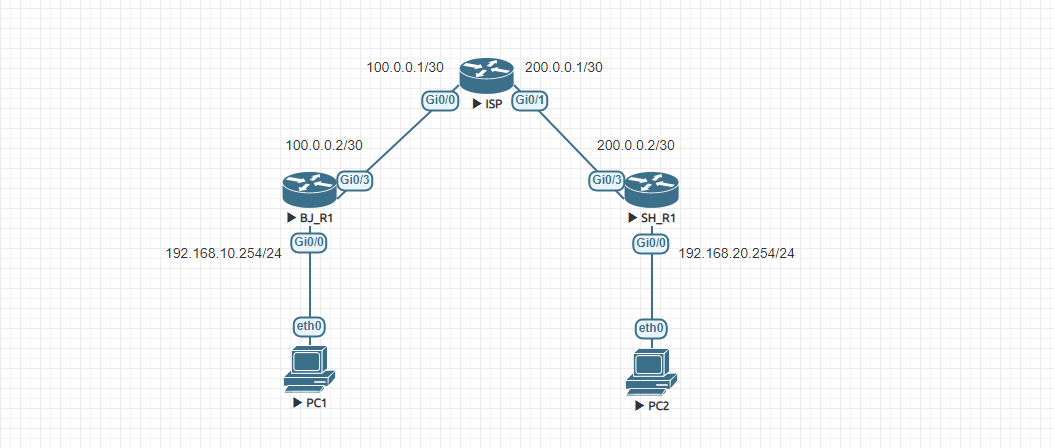
| BJ_R1#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is 100.0.0.1 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 100.0.0.1
100.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 100.0.0.0/30 is directly connected, GigabitEthernet0/3
L 100.0.0.2/32 is directly connected, GigabitEthernet0/3
192.168.10.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.10.0/24 is directly connected, GigabitEthernet0/0
L 192.168.10.254/32 is directly connected, GigabitEthernet0/0
S 192.168.20.0/24 [1/0] via 200.0.0.2
|